Fraudulent document detection: Protect Your Business from Paper-Based Threats

At its core, fraudulent document detection is all about using smart tech to spot invoices, receipts, and other files that have been forged, altered, or completely made up. Think of it as a digital forensics unit for your finance department—a critical defense against scams that can drain your company's bank account.
The Growing Threat of Document Fraud

Imagine your business is humming along, but a silent thief is siphoning off funds. This isn't a dramatic heist; it’s the quiet work of a digitally altered invoice or a pixel-perfect fake receipt. Today, spotting these fakes is an essential business function, not just a back-office chore. We’ve moved way beyond just looking for bad photocopies.
The real challenge now is identifying sophisticated digital forgeries and even AI-generated invoices designed to fool the sharpest human eyes. The scale and complexity of this problem are growing at a dizzying pace.
Why Manual Checks Are No Longer Enough
Relying on human review is like trying to inspect a mountain of paperwork with a single magnifying glass. A person might catch an obvious typo, but they'll almost certainly miss the subtle breadcrumbs of digital manipulation or inconsistencies hidden deep within a document's code.
The sheer volume of transactions most businesses handle makes it impossible to manually scrutinize every single file. Fraudsters know this. They exploit the fact that busy teams often approve payments after just a quick glance. With remote work and digital-first operations becoming the norm, this vulnerability has only gotten wider.
The surge in fraudulent activity is one of the most critical challenges businesses face today. For example, fraudulent identity documents shot up by 72% in just one year, a clear signal of a fundamental shift in criminal tactics. With fakes now coming from over 50 countries, manual verification is simply unrealistic. You can find more details on these identity fraud trends at TrustID.co.uk.
The Shift to Automated Verification
Automated systems are your first line of defense, tirelessly scanning every document for red flags. These tools don’t get tired or distracted. They apply a consistent, rigorous set of rules and advanced analytics to every single file, freeing up your finance team to focus on strategy instead of tedious, repetitive checks.
Automation brings a few game-changing advantages to the table:
- Speed and Scale: Instantly process thousands of documents without creating a bottleneck in your accounts payable workflow.
- Enhanced Accuracy: Detect subtle signs of tampering that are invisible to the human eye, like pixel manipulation or metadata mismatches.
- Consistent Application: Apply the same tough verification standards to every document, every single time, slashing the risk of human error.
This guide is about building a modern defense against this threat. We'll break down how fraud works, why old-school manual processes are failing, and how automated tools can protect your business from serious financial and reputational damage. By understanding these concepts, you'll be far better equipped for analyzing unstructured data from all the documents your business receives.
Recognizing Common Types of Document Fraud

Before you can build a solid defense, you have to understand the attacker's playbook. Spotting document fraud really starts with knowing the common schemes criminals use to poke holes in your payment processes. These tactics almost always prey on the same vulnerabilities: busy teams, manual oversight, and a lack of systematic checks.
By getting familiar with these common threats, you can turn them from abstract risks into tangible red flags your team can actually spot. The goal is to build an instinct—a built-in "pause" button that gets pushed whenever a document just doesn't feel right.
Invoice and Payment Fraud Schemes
Invoice fraud is a massive source of financial loss, and the bad actors have several tried-and-true methods. Each one is designed to look legitimate at a glance, making them especially dangerous for companies that haven't automated their verification.
- Phantom Vendor Invoices: This is a classic. A fraudster invents a fake company, whips up a professional-looking invoice for services you never got, and sends it over. Without a rigorously verified vendor list, it’s alarmingly easy for these to slip through and get paid.
- Inflated Invoices: This one's more subtle. A real invoice from a real vendor gets intercepted and tweaked. The fraudster might bump up the total amount by a small percentage or add a few bogus line items, betting that the changes are small enough to fly under the radar.
- Duplicate Invoices: A simple but shockingly effective trick. An already-paid invoice is just resubmitted a few weeks or months later. Overwhelmed teams might not catch the repeat payment, especially if the invoice numbers are slightly altered or the dates are far apart.
A core principle in stopping payment fraud is dead simple: make sure the goods or services on an invoice match what you actually ordered and received. This one verification step is the foundation of any strong financial control system.
Expense Report and Receipt Fraud
Employee expense fraud is another big headache. It often starts with small, seemingly innocent amounts that add up to a significant problem over time. And now that digital receipts can be altered so easily, it's a growing concern for businesses of every size.
The most common tactics include:
- Fabricated Receipts: Someone just makes up a receipt for a purchase that never happened. Think of a "business lunch" that was really just a template filled out in a PDF editor.
- Altered Amounts: A real receipt gets doctored to show a higher cost. For example, a $20 cab ride is digitally changed to look like a $50 fare, and the employee pockets the difference.
- Mislabeled Expenses: This is where personal spending gets disguised as a business cost. That weekend dinner with friends? It's suddenly relabeled as a "client meeting."
To give your team a better sense of what to look for, here's a quick rundown of the red flags associated with each fraud type.
Key Indicators of Common Document Fraud Schemes
This table summarizes common red flags associated with different types of invoice and receipt fraud, helping teams quickly spot suspicious activity.
| Fraud Type | Common Red Flags | Potential Business Impact |
|---|---|---|
| Phantom Vendor | Missing contact info (phone, address); generic email (e.g., @gmail.com); no purchase order reference; pressure to pay quickly. | Direct financial loss; compromised vendor master file; compliance and audit risks. |
| Inflated Invoice | Amounts don't match purchase order or contract; unusual line items; sudden price increases without notice; poor-quality invoice scans. | Overpayment for goods/services; eroded profit margins; damaged vendor relationships if original invoice was intercepted. |
| Duplicate Invoice | Identical or slightly altered invoice number; same amount and date as a previous payment; invoices submitted across different periods. | Paying for the same service twice; significant cash flow leakage over time; difficulty in financial reconciliation. |
| Altered Receipt | Mismatched fonts or text alignment on amounts/dates; pixelation around key numbers; unusually high amounts for common items (e.g., $100 coffee). | Financial loss from inflated reimbursements; breakdown of internal trust; potential for widespread policy abuse. |
Knowing these indicators is a huge step forward in empowering your team to be the first line of defense against financial leakage.
Building Your First Line of Defense
Recognizing these fraud types is step one, but you need a systematic approach to actually prevent them. Implementing basic checks like two-way matching, where you compare the details on an invoice against the corresponding purchase order, creates a powerful verification layer. This simple cross-check can stop many of these schemes cold.
For a deeper look into this process, you can explore the details of two-way matching in accounts payable and see how it fits into a secure workflow.
Ultimately, the most effective shield is a combination of well-trained employees who know what to look for and smart technology that automates the verification process.
How Modern Fraud Detection Technology Works
How do you catch a forgery that’s invisible to the naked eye? The answer isn't manual spot-checks. Having a person eyeball an invoice is slow, riddled with human error, and completely outmatched by the sophisticated tools fraudsters use today.
Even basic rule-based systems—the kind that flag a missing P.O. number—are easy to trick. They’re like a security guard with a fixed checklist, unable to recognize a clever new disguise. To fight modern fraud, you need a far more intelligent and layered defense.
Instead of relying on a single checkpoint, modern systems analyze a document from every conceivable angle, creating a comprehensive security profile that’s incredibly tough to fake.
The Rise of AI and Machine Learning
Think of an AI system as a veteran detective who has reviewed millions of cases. It learns over time, spotting subtle patterns of fraud that a human would never catch. Machine learning (ML) models are trained on massive datasets containing both real and fraudulent documents, teaching them to identify suspicious traits with stunning accuracy.
This isn't just about ticking off a list of red flags. The AI looks at the entire document in context. It might notice the font used for the total amount is a fraction of a point off from the rest of the text. Or maybe the line spacing is inconsistent with that vendor’s other invoices. These are the tiny, almost imperceptible details that scream "forgery" to a trained algorithm.
“AI-assisted document forgery has emerged as a game-changing threat, with criminals leveraging advanced artificial intelligence to bypass traditional verification systems. The quality and sophistication of these digitally manipulated documents is increasingly high, as photographs of genuine holders or text within documents are being altered with remarkable precision.”
It’s a technological arms race, and businesses need equally advanced tools to keep up. You can read more about how identity fraud is increasing in the age of AI to understand the scale of this challenge.
Digital Forensics Uncovering Hidden Clues
Beyond high-level pattern recognition, modern fraud detection dives into a document's digital DNA. Two key techniques make this possible: computer vision and metadata analysis. They work together like a digital forensics team combing a crime scene for microscopic evidence.
Computer Vision Analysis: This technology scrutinizes a document at the pixel level. It’s looking for:
- Pixel Manipulation: Spotting areas where pixels have been altered, cloned, or added to change numbers or text.
- Compression Artifacts: Finding inconsistencies in how different parts of an image are compressed, a common byproduct of digital editing.
- Font and Layout Inconsistencies: Analyzing the document's structure to find tiny variations in fonts, alignment, or spacing that betray tampering.
Metadata Analysis: Every digital file has a hidden history, or metadata, that tells its story. This analysis uncovers:
- Creation and Modification Dates: Flagging documents that were edited long after they were supposedly finalized.
- Software Signatures: Revealing if a document was opened in editing software like Adobe Photoshop or Illustrator.
- Hidden Layers: Finding concealed text or image layers left behind from the forgery process.
When you combine these methods, you get a complete picture. The AI might flag a suspicious pattern, and the metadata analysis could confirm the file was recently altered with image-editing software. This multi-layered approach creates a robust defense that’s far more effective than any single technique on its own.
Of course, none of this is possible until the system can actually read the document. By turning a visual file into structured, machine-readable data, these analytical tools can get to work. To get a better handle on this foundational step, you can learn more about what data parsing is and how it enables this deeper level of scrutiny.
Ultimately, this combination of AI-driven intelligence and deep file analysis allows businesses to catch forgeries that would otherwise go completely unnoticed, protecting their bottom line from increasingly clever threats.
Putting Automated Fraud Detection Into Practice
Theory is great, but seeing how fraudulent document detection actually works in a real workflow is where the value becomes crystal clear. Adding these tools isn't about some massive IT project; it's about plugging a smart, vigilant service right into your existing accounts payable (AP) or expense management process.
Let's walk through a typical workflow, using a tool like ExtractBill as our example. The goal isn't to replace your team but to empower them. We want to build a system where technology handles the tedious, high-volume checks, freeing up your experts to focus only on the high-risk exceptions that genuinely need a human eye.
This approach completely changes how documents are vetted, shifting from a quick glance to a deep forensic analysis that takes just seconds.
The diagram below maps out this modern, multi-layered approach.
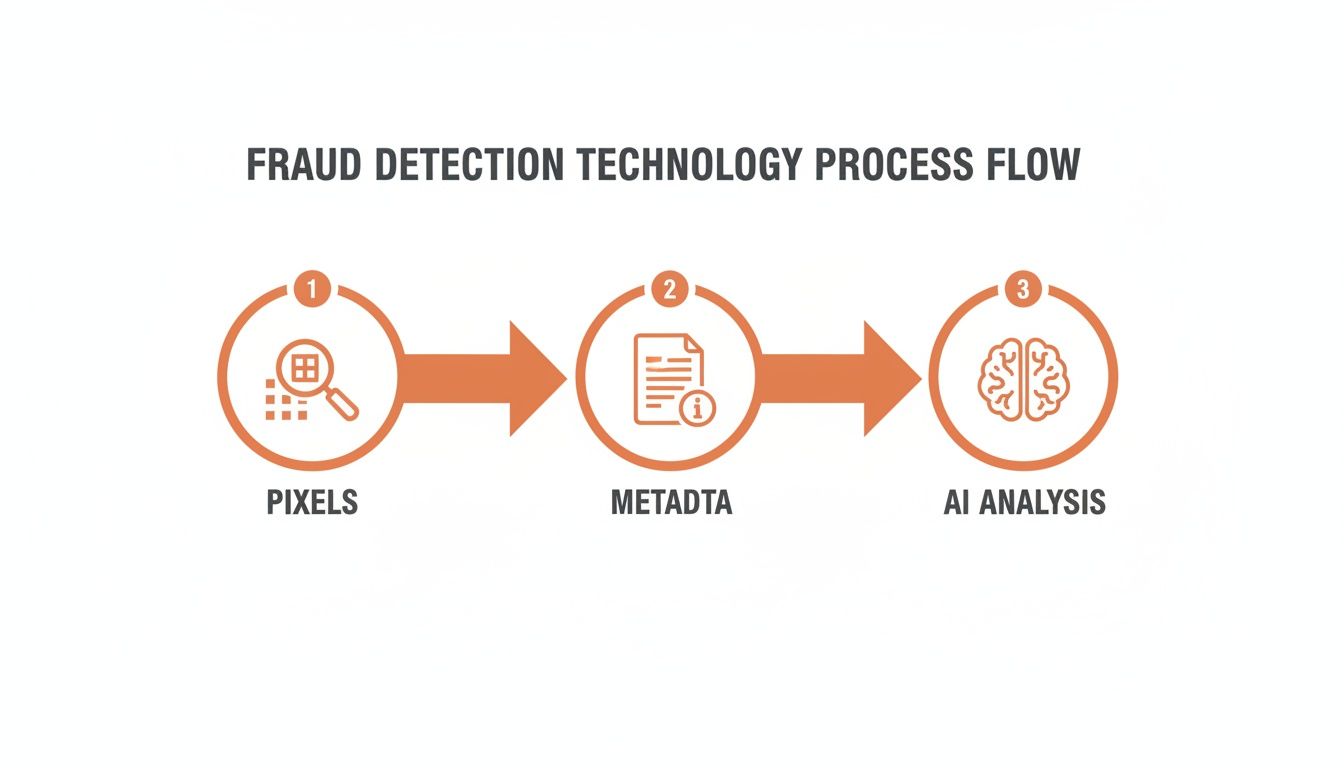
As you can see, a solid defense looks at everything—a document's visual integrity, its structure, and its context—to catch even the most sophisticated forgeries.
The Automated Verification Workflow
The journey from a raw document to a fully verified, payment-ready record involves just a few key stages. This entire cycle, which might take a human reviewer anywhere from a few minutes to an hour, is done and dusted by an automated system in less than five seconds.
-
Document Submission: It all kicks off when a document—a PDF invoice, a JPG receipt—is uploaded. This can be as simple as a drag-and-drop into a web portal or, for bigger operations, a quick API call that programmatically sends the file for processing.
-
Data Extraction and Structuring: First, the system uses AI-powered Optical Character Recognition (OCR) to read the document. It doesn't just grab raw text; it understands it. It pinpoints key fields like the vendor's name, invoice number, line items, and the total amount, neatly converting the messy, unstructured file into clean, structured JSON data.
-
Cross-Verification and Analysis: Once the data is structured, the real detective work begins. The system runs a whole battery of checks at the same time, looking for any and all red flags.
This is the crucial handoff from simple data entry to intelligent security. The system stops asking "What does this document say?" and starts asking, "Does this document make sense, and can I trust its digital fingerprint?"
These checks act like a series of security gates, each one designed to catch a different type of fraud.
The Layers of Automated Checks
An automated platform runs multiple verification techniques in parallel. This combined, layered approach is what gives modern fraud detection its power.
-
Heuristic and Rule-Based Checks: The system first checks for internal consistency. Do the line items actually add up to the grand total? Is the sales tax calculated correctly? It also validates the document against your own business rules, like ensuring the vendor is on your approved list or flagging an invoice that blows past a set spending limit.
-
Historical Data Comparison: Next, the platform compares the document to past submissions from that same vendor. It's looking for anything out of the ordinary—a sudden change in banking details, a completely new invoice template, or payment terms that don't match previous agreements. These subtle shifts are classic signs of account takeover fraud.
-
Digital Forensic Analysis: Finally, it digs into the file's "digital DNA." This involves scanning the metadata for traces of editing software (like Photoshop), analyzing pixel patterns for tell-tale signs of tampering, and spotting inconsistencies in fonts or image compression that scream "this has been altered."
Once these checks are complete, the system delivers the structured data along with a risk score or specific flags that pinpoint potential problems. Low-risk documents can be automatically passed to your accounting software for payment. High-risk documents? They get routed directly to your AP team for a final human review. This creates a highly efficient "human-in-the-loop" process.
You can learn more about how to automate your document workflow to see how all these pieces fit together. By setting up a system like this, you build a powerful, scalable, and consistent defense against fraud that lets your team work smarter, not harder.
Manual vs Automated Document Verification
The difference between sticking with old-school manual reviews and adopting an automated solution is stark. It's not just about speed; it's about a fundamental shift in accuracy, scalability, and security.
The table below breaks down the key differences.
| Feature | Manual Verification | Automated Verification (e.g., ExtractBill) |
|---|---|---|
| Speed | Slow; minutes to hours per document. | Extremely fast; under 5 seconds per document. |
| Accuracy | Prone to human error, fatigue, and oversight. | Highly accurate; consistent checks eliminate typos and missed details. |
| Scalability | Poor; requires hiring more staff to handle increased volume. | Excellent; scales instantly to handle thousands of documents. |
| Fraud Detection | Limited to obvious visual fakes; misses digital alterations. | Deep forensic analysis; detects metadata, pixel, and font tampering. |
| Cost | High labor costs; expensive to scale. | Low per-document cost; predictable and budget-friendly. |
| Audit Trail | Manual and often inconsistent record-keeping. | Automatic, detailed logs of every check performed on every file. |
| Consistency | Varies by reviewer and time of day. | Every document is checked against the exact same rules, 24/7. |
| Team Focus | Employees bogged down in repetitive, low-value data entry. | Employees focus on strategic, high-value tasks and exceptions. |
Ultimately, while manual verification was once the only option, automated systems now offer a more robust, reliable, and cost-effective way to protect your business from document fraud while boosting operational efficiency.
Building Your Human Firewall Against Fraud
While the right technology gives you a powerful shield against document fraud, it’s only half the battle. Your strongest, most adaptable asset is a well-trained, security-conscious team. It’s time to build a "human firewall."
This isn't just about another training seminar. It's about weaving specific processes and a culture of vigilance into your company's DNA, creating a system where your automated tools and your people work together. It’s about turning potential targets into your first and best line of defense, empowering them to spot the subtle red flags that even the smartest software might miss.
And the stakes are sky-high. Globally, companies lose an average of 7.7% of their annual revenue to fraud. For businesses in the U.S., that number jumps to a staggering 9.8%. Schemes like synthetic identity fraud and document manipulation are a huge part of the problem, accounting for 20% of all reported business fraud losses. These aren't just abstract statistics; they represent real money walking out the door. You can dig into more of the numbers in TransUnion's global fraud report.
Implementing Essential Procedural Safeguards
Building a human firewall starts with embedding a few non-negotiable procedures into your daily operations. Think of these as intentional friction for fraudsters that actually make legitimate work smoother.
Here are the foundational practices you need to implement now:
-
Separation of Duties: This is the absolute cornerstone of preventing internal fraud. The person who approves an invoice should never be the same person who processes the payment. It’s a simple division of labor that creates a natural check-and-balance, and it can single-handedly stop a bogus payment.
-
Maintain a Verified Vendor Master File: Your vendor list needs to be a fortress, not an open directory. Create a rock-solid process for vetting and adding any new vendor, which must include independently verifying their contact info and banking details. This shuts the door on "phantom vendors" created purely to siphon money.
"A proactive, layered security approach that combines people, processes, and technology is the most effective way to mitigate fraud. Relying on any single element leaves dangerous gaps for criminals to exploit."
Fostering a Culture of Vigilance
Controls and procedures are only as good as the people following them. A security-first mindset isn't built overnight; it comes from ongoing effort and clear communication that turns abstract policies into ingrained, everyday habits.
A truly vigilant culture rests on two pillars:
-
Ongoing Employee Training: Fraud tactics evolve constantly, so a one-and-done training session is useless. Hold regular workshops using real-world examples of doctored invoices and receipts. Teach your team to recognize red flags like sudden changes in vendor bank details, unusual payment requests, or someone pressuring them to bypass the standard approval process.
-
Unpredictable Audits and Reviews: Nothing keeps people sharper than knowing their work might be reviewed at any time. Conduct regular, randomized audits of payments and expense reports. The possibility that any transaction could be scrutinized encourages everyone to stick to the rules and makes it incredibly difficult for fraud—internal or external—to go unnoticed. You also need to create clear, confidential channels for employees to report anything suspicious without fearing reprisal.
When you combine these human-centric strategies with automated fraudulent document detection, you build a defense that’s truly layered. Your tech will catch the technical forgeries, and your empowered team will catch the contextual red flags. Together, they’ll protect your business from every angle.
Got Questions About Document Fraud? We Have Answers.
Jumping into fraud detection can feel a little overwhelming. Where do you even begin? Can you really trust an algorithm to protect your business? And how does this kind of tech play nice with the accounting software you already use?
Let's clear things up. Here are straightforward answers to the most common questions we hear.
What’s the First, Most Impactful Step My Business Can Take?
Start by centralizing your document intake. It’s a simple change with a massive impact.
Instead of invoices and receipts flooding a dozen different inboxes, create a single, controlled entry point. This could be a dedicated email address (invoices@yourcompany.com) or an automated platform that everything funnels into. Right away, you’ve created visibility over every single document that comes through the door.
Next, add a basic vendor verification step to your process. Before paying a new vendor for the first time, make a quick confirmation call to a contact you trust. The key here is to use a phone number you already have on file, not the one printed on the new invoice. These two small procedural tweaks can shut down a surprising amount of fraud before it even starts, all with minimal effort.
Can AI Detection Completely Replace Human Review?
Nope, and it’s not supposed to.
Think of AI as your smartest, most tireless front-line soldier. Its job is to scan every single document—thousands of them—for the tiny red flags and inconsistencies that a human reviewer would eventually miss. It filters out all the legitimate noise and flags only the handful of documents that genuinely need a second look from an expert.
The gold standard is a "human-in-the-loop" system. Let the technology handle the sheer volume and deep analysis, then empower your finance team to apply its critical thinking and business context to the flagged exceptions. You get the best of both worlds: machine-level accuracy combined with irreplaceable human judgment.
This partnership lets you catch sophisticated fraud without grinding your operations to a halt. Your team’s expertise is focused exactly where it matters most, making them more effective than ever.
How Does This Tech Integrate with My Accounting Software?
Modern fraud detection services are built to plug right into your existing workflows using APIs (Application Programming Interfaces). You don't need a massive IT project to get it working.
The process is refreshingly simple:
- Send the Document: Your system shoots a file, like an invoice PDF, over to the service's API.
- Get Back Structured Data: In seconds, the service extracts all the data, runs a full fraud analysis, and sends back clean, structured information (usually in JSON format) complete with risk scores and specific warning flags.
- Automate What's Next: This clean data can then automatically populate fields in your accounting software, whether it's QuickBooks or Xero. High-risk documents get routed for manual approval, while trusted ones flow right through.
This approach embeds powerful fraud detection directly into the tools your team relies on every day, creating a seamless process from receipt to reconciliation.
Ready to stop manual data entry and secure your financial workflows? With ExtractBill, you can convert any invoice or receipt into clean, structured data in seconds. Get your first three document extractions free at ExtractBill.
Ready to automate your documents?
Start extracting invoice data in seconds with ExtractBill's AI-powered API.
Get Started for Free